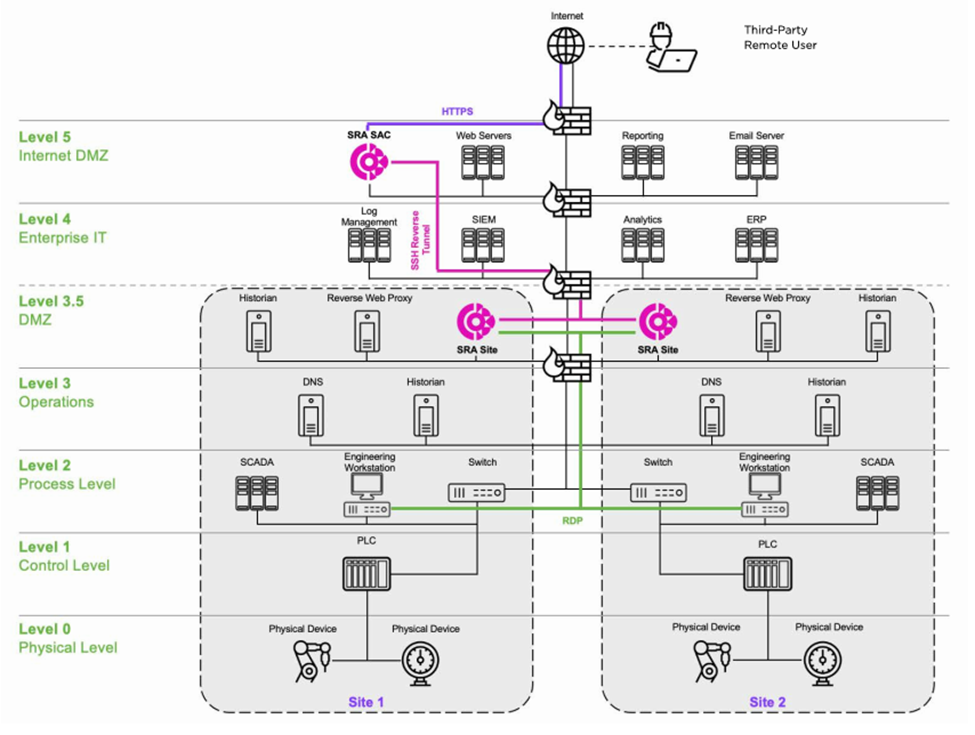
(OT SRA) is a solution designed specifically for industrial and production environments (Operational Technology - OT), which enables secure and efficient remote access to OT systems and devices. The goal is to provide secure access for process engineers, contractors, and other authorized users who need to manage, monitor, or troubleshoot systems in an industrial environment while minimizing the risk of cyber threats.
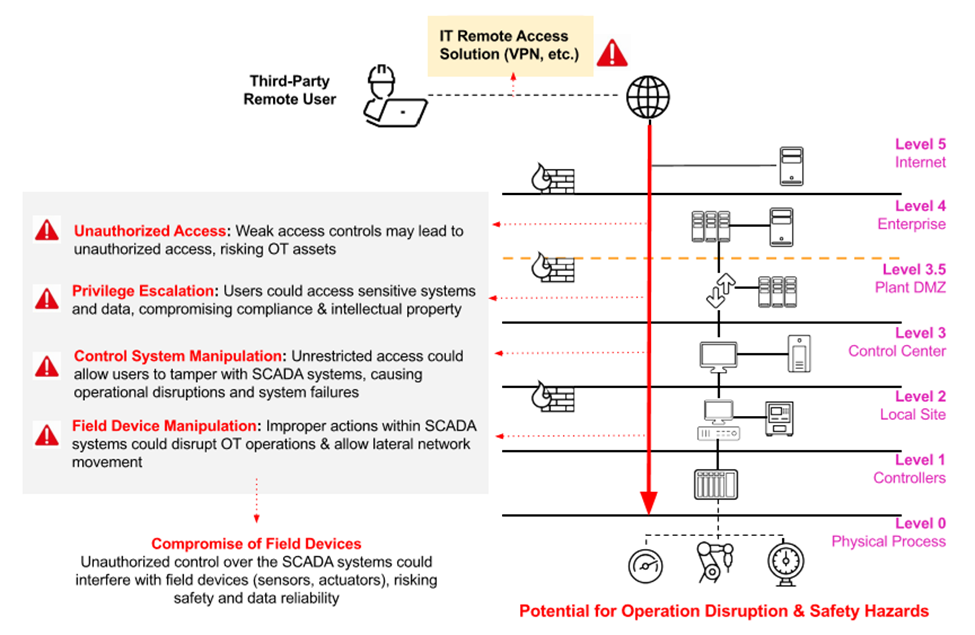
OT Secure Remote Access is a key tool for modern industrial and manufacturing companies seeking to improve the efficiency of maintaining and managing their OT systems without compromising security