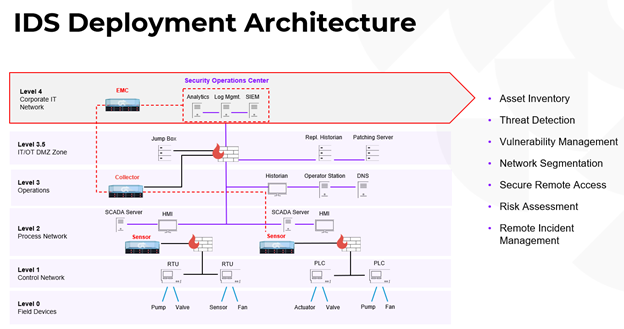
Accura implements OT IDS (Intrusion Detection System) in critical infrastructure by deploying advanced sensors and monitoring technologies in SCADA ICS / DCS that detect anomalies and potential threats in real time.
Why it is necessary to have visibility in the OT network
-
You cannot protect what you cannot see. Accura offers and implements industrial cyber security solutions such as network threat detection (Intrusion Detection System) and other cyber technologies for threat detection.
-
Without an IDS, an attacker can be resident in an OT network for up to 160 days on average and achieve incredible freedom and lateral movement allowing significant disruption of production processes when you least expect it.
-
Good detection enables better response, and better response enables even better prevention against cyber threats that can have devastating effects on control systems.