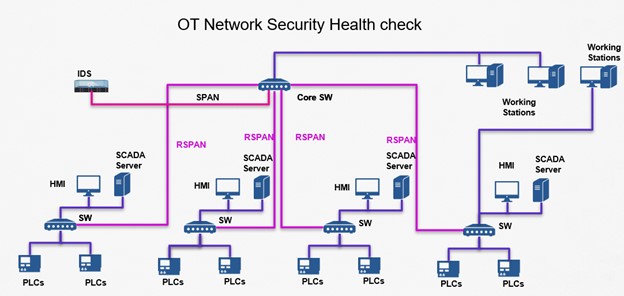
With the help of IDS (Intrusion Detection System), we identify threats, vulnerabilities, and risks in control systems within the agreed time frame.
Identifying potential attack vectors of how an attacker would progress into your OT network with a graphical representation of the attack based on the Purdue Model architecture.
The probe will provide detailed information about assets in the OT network and exploitable vulnerabilities.
Developing a final report on the cyber hygiene and health of your OT network with recommendations.